classification
exclusiveForwarding and redirecting black box penetration testing guidance
forward(forward)
It is a jump on the server side, where a request is sent from the client to the service...
Free exclusivePenetration testing guidance document contains attacks
1. Attack scenario
File inclusion attack
described
The file contains vulnerabilities that are "code notes...
Free boutiqueChuangsheng Series Qiankun Mutual Entertainment Club Room Cards and Chess + Video Building Tutorial
This is the second modification of Guizhou Mahjong, which removed Guizhou Mahjong. Niu Niu, three male and golden flowers all bring accompanying robots
Golden Flower machine...
boutiqueUniversal modification tutorial for the PC controller of Netfox video game series
Universal modification tutorial for the PC controller of Netfox video game series
Many people will not change this control terminal, so they specially recorded this tutorial for...
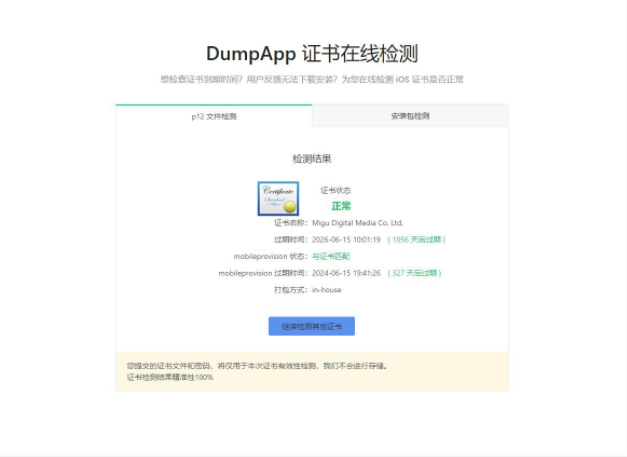
boutiqueApple Signature Certificate IOS Enterprise IPA Software Certificate valid until 2026
Some time ago, I shared an ios certificate that is valid until 2025, this time this one is until 2026
For likes to install...
boutiqueFutureTask 2 in Java
1. The first two chapters of the preface briefly analyze the Future interface and FutureTask. This article will introduce the use of FutureTask...
Free exclusiveBlack Box Penetration Testing Guide: XML Injection
I. attack scenarios
Send XML requests directly
described
Many application systems or components require...
Free exclusiveBlack Box Penetration Testing Guide Cross-site Forging Request CSRF
CSRF ( Cross Site Request Forgery) is a Web application attacker...
Free exclusiveDownload penetration testing guidance
attack scenarios
Download without defense
Description:
Many application systems or components provide...
Free boutiquePrinciples of Java Code Generator
1. Foreword I wrote an article about the Mybatis Plus code generator a few days ago, and many students privately asked me about this code...
Free boutiqueSubscription and publishing model in Java programming
1. Foreword Quick Hand released "Seeing" the day before yesterday, received rave reviews, overshadowed the previous "Hou Lang". Nowadays, inside...
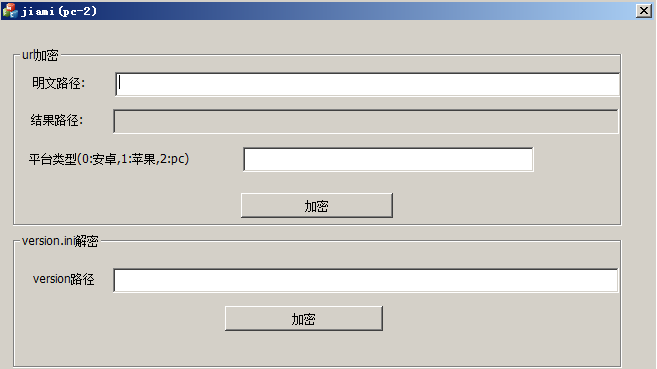
Free boutiqueAowan series client universal encryption and decryption tool
Faced with the rapid development of network security technology, AoPlay has launched a new generation of client-side universal encryption and decryption tools to solve...
exclusiveBlack box penetration testing guidance passed down
I. attack scenarios
Upload webshell directly
Describe many application systems...
Free boutiqueUnder what circumstances cannot Java generics be used
1. Introduction Java 1.5 introduces generics to ensure type safety, prevent type conversion exceptions at run time, and allow classes to...
Free